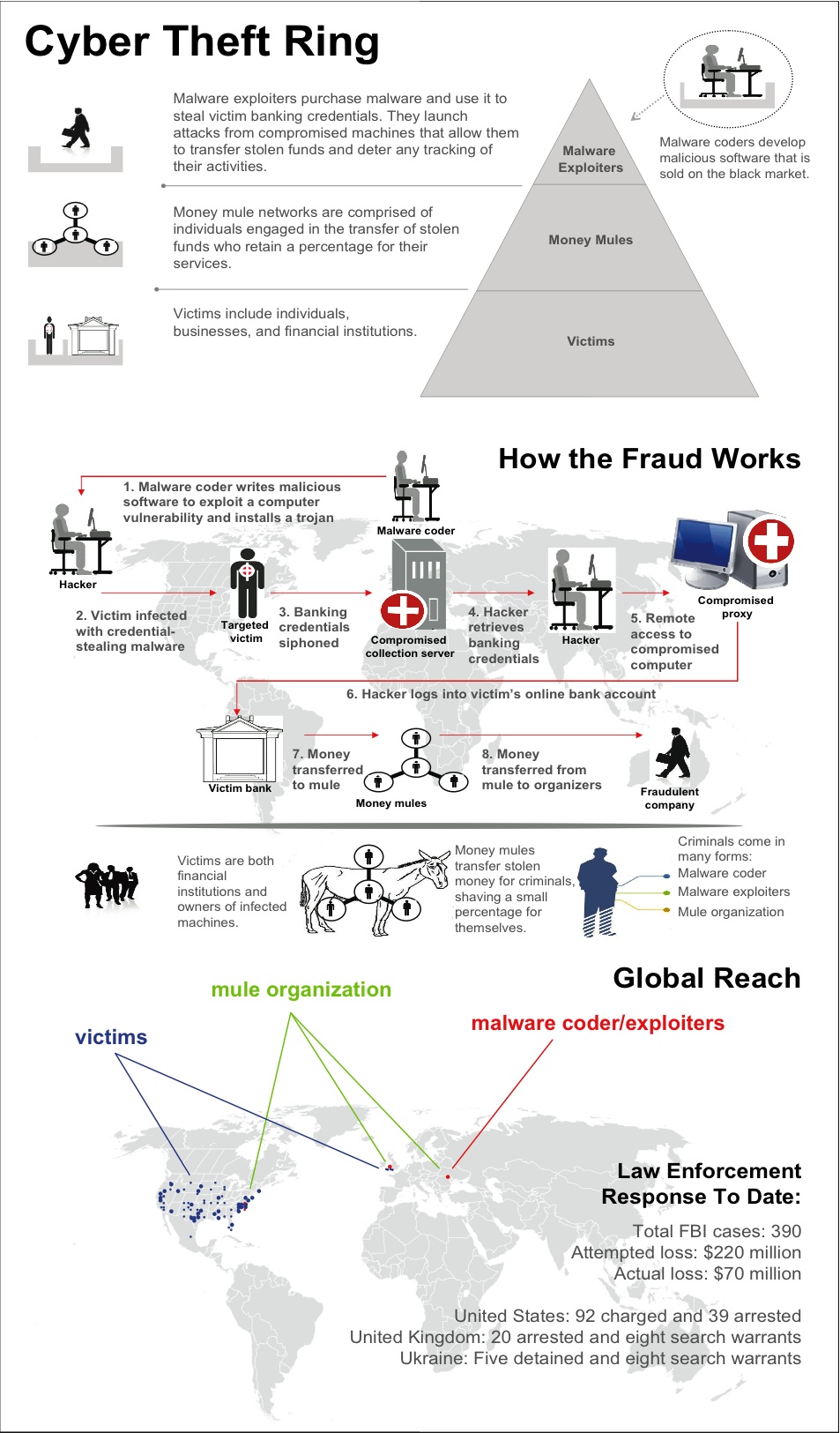
Case Study: Zeus Trojan
Zeus is considered a banking Trojan that runs exclusively on Windows. The software primarily works to steal the host's banking credentials. The first versions did this by logging the input keys of an infected computer, accessing the users browser information and accessing the protected information of the browser. It also automatically adds the computer to a botnet. It is estimated to have infected over 3.6 million computers in the US and over 960 different banks. It is quite difficult to detect using even advanced anti-virus software and continues to be actively developed. Versions of are available for purchase on the Dark Net. What is peculiar about Zeus is that it is rented out to various cyber criminals for a nominal fee. The operator exerts significant control over the malware and typically charges $3000-4000 for the malware. To use the malware, one needs to obtain an authorization code from the operator, which is a license to use a specific version of the trojan. Over time this has led to many new features being added to the Trojan. All add-ons cost money and these add-ons are source of the great amount of variation in Zeus samples. Among the features that can be added include: Steal data submitted in HTTP formssteals X.509 Public Key CertificatesModifies HTML pages for information stealing purposesRedirects users to pages controlled by the attackerDownload and execute arbitrary programsEmploy a randsomware such as LockBitPrices for several features are:$1500 for BackconnectThis feature allows the user to interact with the targeted computer to, for example, monitor the screen or recieve active key events.$10,000 for Virtual Network ModuleThis feature allows the attacker to take over the infected computer and completely control it without the user knowing.$2000 for Windows 7 SupportThis module allows an attacker to employ Zeus on Windows7/Vista machines, instead of only XP. |
 |
|---|
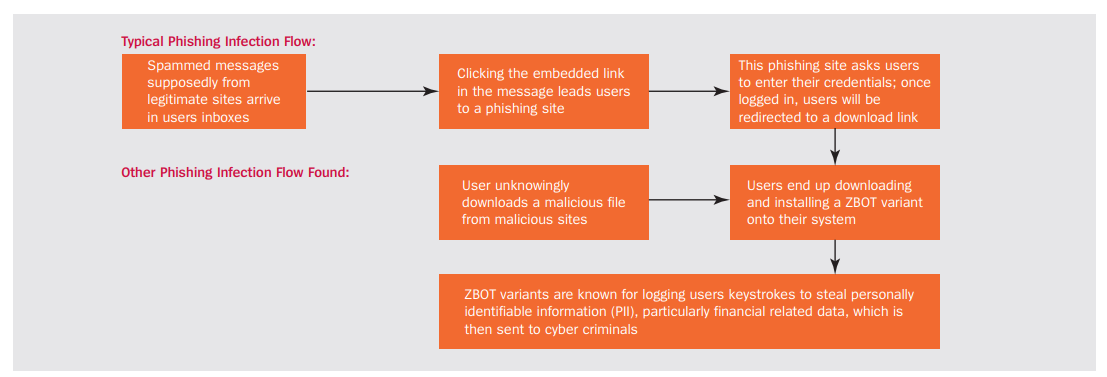
Infection by ZeusAny number of vectors can be used to infect a victim with Zeus. The most common are executables in e-mal attachments, links that download the trojan. This allows the attacker to directly eavesdrop on the host and obtain their banking credentials. Alternatively, Zeus is able to intercept the communications of the host and using phishing techniques, take the the victims banking credentials. |
 |
|---|
Zeus Virus |
Philip Krause |
|
|---|