Modular Structure
The WannaCry randsomware can be broken down into three modular pieces,
each utilizing a different exploit/vulnerability.
1. The Worm
Upon infecting a host, WannaCry starts to scan the local network
and random IP addresses on the internet. It does so to find ones
using the Microsoft SMB protocol. This protcol is used by Windows to
share documents between computers. It is at this point that
it employs the EternalBlue exploit. EternalBlue had existed for several
years before the advent of WannaCry, and it was only WannaCry
that forced the NSA to inform Microsoft of the vulnerability. It
works by exploiting the way some versions of Windows mishandle certain
packets to allow an attacker to execute code on the target. This element
allows it to copy and execute itself on remote computers.
2. The Kill Switch
Once WannaCry finds a target it drops the file mssecsvc.exe which then executes
tasksche.exe, the Kill-switch checker. If the server does not
exist then it proceeds to install the DOUBLEPULSAR backdoor. This allows
it to gain persistence after which it installs the payload.
3. The Payload
After the intial check, tasksche.exe continues by searching the hosts
files for directories starting with single letters such as C:/ and etc.
It proceeds to encrypt them using 2048-bit RSA and make a new directory.
Inside this newly created directory it adds several helper .exe files including
tor.exe. After running it tor.exe, the malware connects through a tor node
to hide the operators of WannaCry. Upon encrypting all the files,
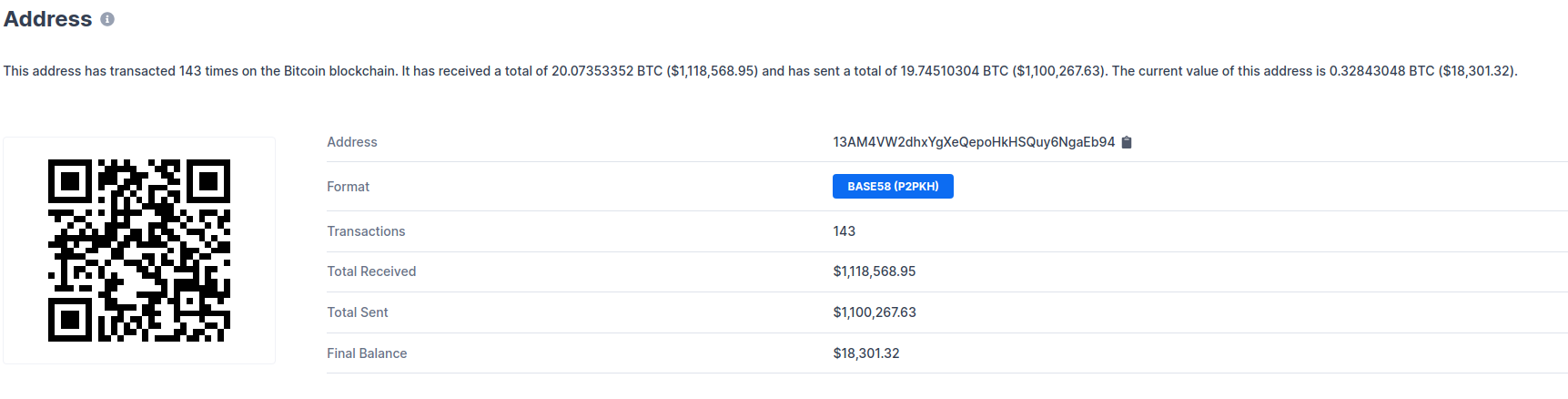
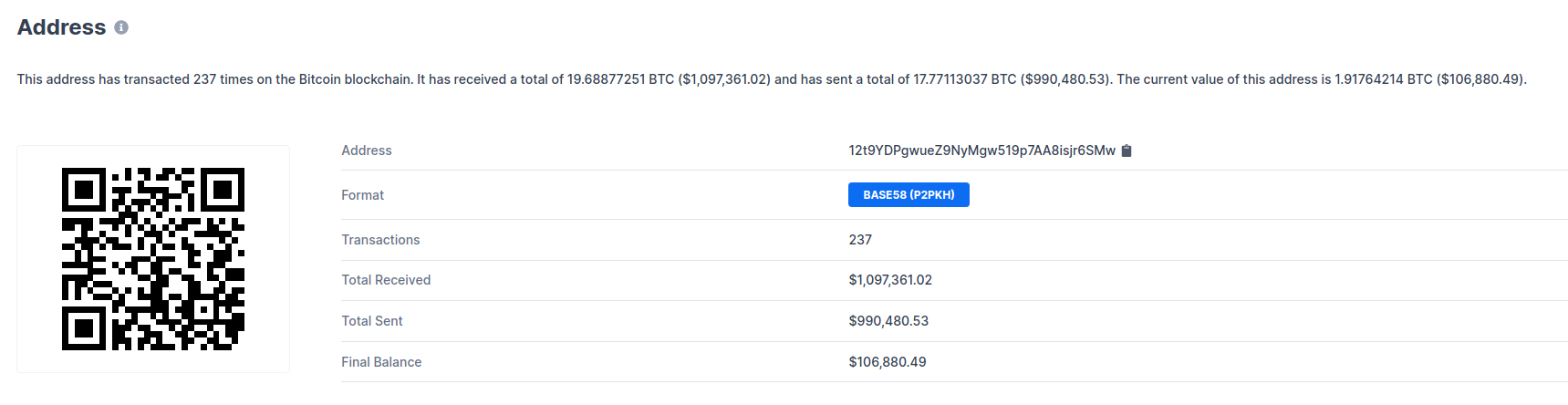
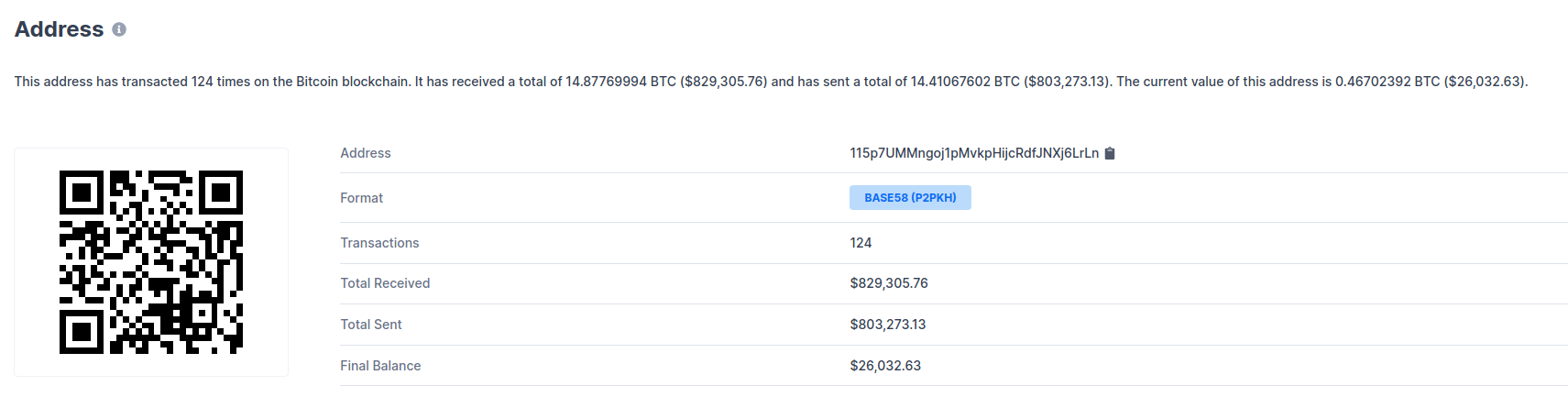
it produces the red randsome note senn on the previous page. This note
instructs the victim to transfer $300 of BTC to a BTC wallet.
|