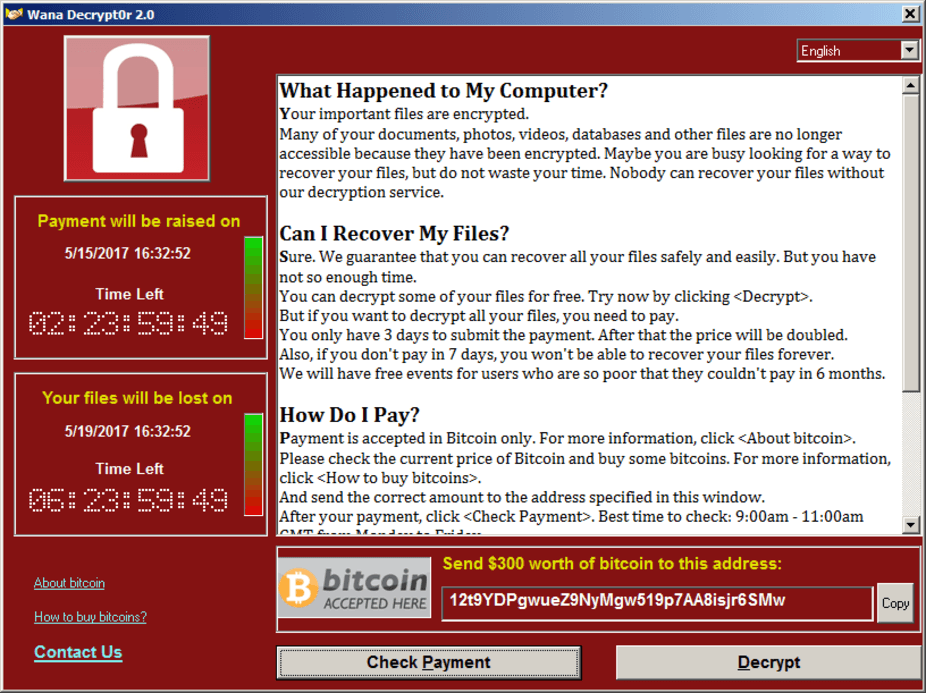
Timeline of the Attack
The initial attack started on Friday the 12th of May. The worm
started spreading from Asia and before the end of the day was able to
infect more than 200,000 computers worldwide. Among the most
notable targets was the British National Health Service, FedEx, O2,
Taiwan SemiConductor and MegaFon. All targets were severly impaired,
rendering their IT infrastructure unusable. In particualr the NHS
was forced to close emergency rooms and limit patient care due
their whole network being down. The degree of damage and speed with which
it was caused remains among the greatest of any cyber attack.
All virus victims were running older unpatched versions of Windows. Microsoft
released a security patch on the same day. Although
this helped patch the exploited vulnerability on uninfected hosts
it was of no help to ones already infected. Despite its quick
spread the initial outbreak was stopped by secuirty researcher
Marcus Hutchins.
This was entirely due to him finding a domain associated kill-switch
in the intial variant. Because at first WannaCry pinged www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
a
domain that did not exist,
it would automatically encrypt the users files. When Hutchins registered
the domain, the virus automatically stopped spreading.
This worked for some time until the domain was targeted by Mirai botnet, with
the hopes of taking it down and allowing WannaCry to continue operating.
2 days later the first variant appeared.
This variant also employed the same kill-switch method albeit with a different
domain. However the continued useage of this same kill-switch mechanism effectively
rendered subsequent versions easier to deal with. Within a week
researchers were able to develop tools to decrypt the files encrypted by
WannaCry and remove it. This effectively stopped its rapid spread. However,
it continues to morph and newer versions have since appeared. Looking at the
3 bitcoin wallets associated to the original variant it appears that some people
continue to pay the ransom.
|